Let's Talk About Your Needs
Subscribe Now! Get Awesome Monthly Posts
Make your business more successful with latest tips and updates for technologies
Uber Suffers Major Cyberattack: Sensitive Data of Millions Exposed
Popular ride-sharing service provider company Uber was hacked in what appears to be an identity-based attack compromising its internal systems and networks.
The ride-sharing giant had to take down a number of its critical systems following a social engineering attack (identity-based). According to the report, Uber’s employees were unable to access the company’s various internal communication and project management tools after the breach.
Uber’s communication team took to Twitter to confirm the breach.
Understanding the Anatomy of the Uber Cyberattack
According to a report by NYT, the attacker phished an Uber employee to gain access to the company’s corporate VPN. The attacker gained network access by sending text messages posing as an official IT admin to gain their credentials before breaching the company’s internal systems. The attacker was able to establish and gain a foothold into a majority of Uber’s internal systems and resources after scanning the company’s internal corporate network where they found user credentials for Uber’s Thycotic account (PAM solution) through a shared network resource and identified a PowerShell script that contained privileged credentials. These credentials provided the hacker with further access to various services and systems of the company’s network.
The attacker was then able to access Uber’s AWS, GSuite, Slack, VMWare, Windows, OneLogin, and Duo environments bypassing the 2FA mechanism for almost anything. Further, according to the Bleeping Computer, the attacker accessed and took data from Uber’s HackerOne bug bounty program, which could be lethal for Uber if it contains unpatched or undisclosed vulnerabilities in the application. The attacker then went on to use Slack for sending a phishing message to Uber employees stating compromised resources.
Why Uber’s cyberattack is a stark reminder for businesses to get serious about cyber security services?
This is not the first time that Uber has found itself in troubled waters, since the ride-hailing giant suffered a similar fate in 2016 when data of 57 million user accounts were compromised after a breach on the company. The company was fined a whopping $150 million for covering up the breach.
The hacker allegedly boasted about how they leveraged the MFA (Multi-Factor Authentication) fatigue as a weapon. MFA serves as a worthy layer in network defenses. However, Uber was using the ‘push notification’ feature where the targeted employee was spammed with these notifications for more than an hour. The hacker then posed as the company’s IT team and told the employee that they need to accept the authentication.
This appears to be an MFA phishing attack, which led to the discovery of a PowerShell script containing admin credentials to Thycotic PAM tool. All the credentials were a part of this PAM tool, the entire organization’s internal systems and networks were compromised since the PAM served as a backdoor to Google Workspace, Amazon Web Services (AWS), Slack, and more. The attack has exposed a huge amount of data pertaining to both drivers’ and customers’ personal data.
Preliminary lessons from the Uber cyberattack
Uber breach is a stark reminder that this type of attack can happen to any organization – regardless of its size, location, or industry. Yes! Such a breach tactic has resulted in the compromise and exposure of critical data for Okta, Microsoft, and Twitter as well, since they have been hacked in a similar manner in the past.
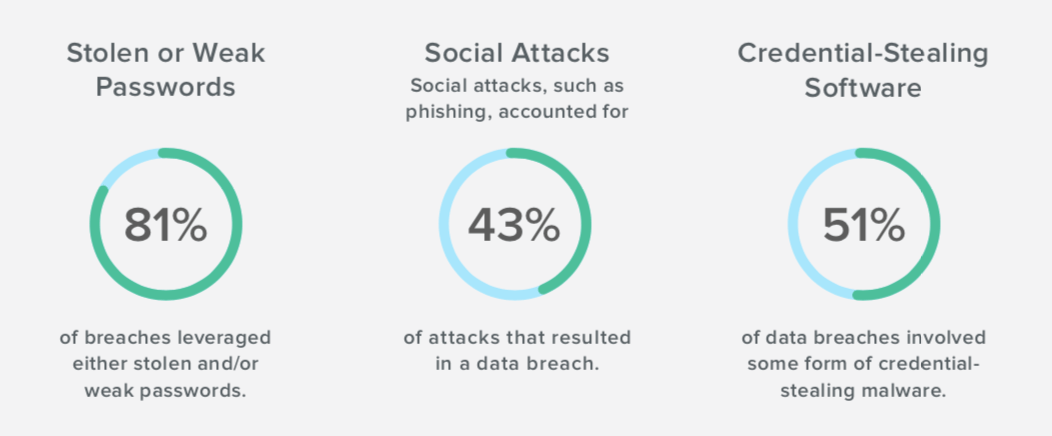
More than 80% of all data breaches involve credentials that are stolen via social engineering tactics or hacked using brute force.
Hackers are evolving quickly and are coming up with new attack tactics. Security teams ought to ensure and deploy trusted cyber security services that leverage advanced threat intelligence to keep such attacks at bay.
Futurism recommends the following cybersecurity measures to keep cyberattacks at bay:
Zero trust security architecture
Identity And Access Management Solution (IAM) with an agile multi-factor authentication
Have a strong endpoint security solution
Insider threat solution & insider threat management
Hunt for advanced threats with an intelligent threat detection (SIEM)
Encrypt critical business data with robust data protection and monitoring
Take regular data backups
Have a disaster recovery plan (DLP)
Have powerful firewall protection
Update OS and antivirus software regularly
Patch vulnerable ports, systems, networks, devices, etc.
Extended detection and response (XDR)
Partner with a trusted managed cyber security services provider that is equipped with a state-of-the-art C-SOC
Create and ensure proper cyber awareness among the staff
Takeaway
The widespread and ubiquitous access that employees today have to internal systems ought to be a chief concern for security teams around the world. The Uber incident is a wake-up call for businesses to get serious about Zero Trust cyber security services.
Attackers are becoming creative and nimble, whereas organizations struggle to keep up with the evolving threat landscape when it comes to ramping up their security posture. One of the smartest means to thwart off these attacks is to seek expert help from a trusted cyber security services provider that can offer the right layers of protection by deploying cyber security monitoring services.
It’s time businesses leverage advance threat protection that leverages market-winning threat intelligence technology and tools to strengthen their security posture and getting help from a cyber security services provider can help achieve that by serving as an extended arm for your IT and security team.
Disclaimer: All the opinions, information, and views expressed in this article are those of the authors and the respective web sources, and in no way reflect the principles, objectives, or views of Futurism Technologies in any way.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.